Before diving in, I’d like to acknowledge our amazing partners in this research, DGTech and Transportation Research Center Inc., and share a quick disclaimer. This material is based upon work done in partnership with DGTech and Transportation Research Center Inc., and supported by National Highway Traffic Safety Administration (NHTSA). Any opinions, findings, conclusions, or recommendations expressed in this material are those of the author(s) and do not necessarily reflect the views of the NHTSA or U.S. Government.
As vehicle electronic and computing systems have grown more and more complex and interconnected over time, they have also grown more susceptible to the threat of cyberattacks. Hundreds of cyberattacks on automotive Electrical and Electronics (E/E) systems have been reported over the last decade, including recent cases in which hackers were able to unlock, start, or even gain remote control of electric vehicles (EVs). Even more worryingly, the frequency and sophistication of these sorts of attacks appears to be growing every year.
Despite this rising threat, little solid data exists on industry-wide patterns of automotive E/E design and cybersecurity resilience. Aiming to fill this critical information gap, earlier this year Galois undertook a project for the National Highway Traffic Safety Administration (NHTSA) exploring how automotive Electrical and Electronics architectures have changed over time, viewed through the lens of cybersecurity. In the end, we created a report that includes models of relevant E/E architectures in Architecture Analysis and Design Language (AADL) and an analysis of past, present, and extrapolated future automotive cybersecurity trends. This article serves as a short summary and exploration of our methodology, findings, and recommendations.
Evolution of Vehicle E/E Architectures
Early automobiles were mostly mechanical with very few, if any, electrical components. The first reported automobile, designed by Karl Benz in 1885, had only a spark plug and a battery. However, as time passed, cars evolved to offer more comfort, luxury, safety, connectivity, and automation. As a result, the number of electrical and electronic components in cars has increased significantly, including Electronic Control Units (ECUs) for computing and control, sensors and actuators, and other electronics. This complex network of components and their interconnections forms the vehicle’s E/E architecture. And as cars become even more feature-rich, the constantly evolving E/E architecture continues to get more and more sophisticated.
Older E/E architectures had only a few components—mostly sensors, actuators, and ECUs with a very specific function like controlling the engine, locking doors, controlling airbag deployment, and so on. As the number and complexity of components increased, E/E architectures tended towards a hierarchy often centered around functional domains like powertrain, autonomous functions, infotainment, interior lighting, and comfort (body domain), etc. Current industry trends indicate that the most sophisticated architectures might be nearing their limits due to cost and complexity constraints, signaling a likely move towards consolidation. Indeed, the most recent architectures are supported by fewer but more powerful and general purpose ECUs and emergence of complex software architectures.
Evaluating E/E Cybersecurity and Resilience
Naturally, this rapid increase in sophistication of E/E components and complex software makes it imperative for the automotive industry to consider the corresponding potential cybersecurity implications. In this project, we delve into this issue by examining and evaluating the cybersecurity and resilience of E/E architectures across different Original Equipment Manufacturers (OEMs), brands, and models manufactured between 2010 and 2020 (14 OEMs, 16 brands, and 23 models).
Our approach was broadly divided into data collection, modeling, and analysis. We surveyed the state of E/E architectures and trends using a select list of vehicles that provide adequate coverage. For every vehicle, we collected data from repair manuals and cross checked with marketing releases. All of these were publicly available sources, though sometimes paywalled. Using this data, we modeled each vehicle’s architecture using AADL. These AADL models were analyzed semi-automatically for their architecture features, cybersecurity, and resilience. We classified the surveyed architectures into classes and qualitatively described their cybersecurity and resilience. Our results and conclusions are based solely on publicly accessible information, and we do not compare or rate individual vehicles’ cybersecurity and resilience.
Vehicle Selection
As a first step, we identified a list of vehicles that are representative of the market size using sales data; higher sales indicated a more popular model. Since we also wanted variation in the E/E architectures, we diversified our list along different makes, geographical locations, and price segments; oftentimes digging into the architecture details to avoid selecting similar ones. Though we wanted a rich variety of architectures, we did not focus on one off or rare architects as they would not have helped us in establishing broad market trends. For the purpose of reporting, we grouped the models into three generations corresponding to models produced around the years 2010 (gen1), 2015 (gen2), and 2020 (gen3).
Data Collection
After compiling a list of selected vehicles, our next step was to gather data on their E/E architectures. However, this proved to be a challenging task since we were limited to publicly available sources. After some research, we found that under the program constraints, the best (though suboptimal) sources were wiring diagrams from repair manuals used by mechanics for maintenance. The information provided by these wiring diagrams was inconsistent across different makes, and it varied between models from the same make over the ten-year period. Additionally, the level of detail was unreliable as relevant information was often missing while other irrelevant information cluttered the diagrams. While we ultimately managed to create an AADL model for every vehicle model, it was a time-consuming, manual process that could not be easily automated.
Snapshot of Findings
So what did we find? While vehicle models across the board display a diverse range of components (modules and buses) utilized, over the past decade, there has been a significant increase in the average number of modules in vehicles (Figure 2), with a more drastic increase seen between Generations 2 and 3. This can be attributed to the addition of new ADAS domains and associated modules. The minimum number of modules has risen from approximately five modules for Generation 1 to roughly 20 for Generation 3, depicted by the elevated floor. To accommodate this surge in modules, new buses have been introduced, as shown in Figure 3, reflecting an overall slow increase in the center of mass of the scatter plot.
As the number of modules and buses increase, so do the cybersecurity implications and potential vulnerabilities. One metric of architecture cybersecurity can come from the notion of component connectivity, a metric that measures the number of modules directly connected to a bus. The higher the average connectivity, the greater the risk of a cyber-attack, as one compromised component could grant access to all components on a bus. Surprisingly, recent analysis indicates that the average number of components per bus has been decreasing steadily from 2010 to 2021, even as the number of components per vehicle has been increasing. This suggests that vehicle manufacturers are taking steps to improve the segregation of components and reduce the risk of cybersecurity threats.
Finally, we leave readers with figure 5 that illustrates the difference in the number of modules across model generations.
Case study of Ford F-150’s Architecture
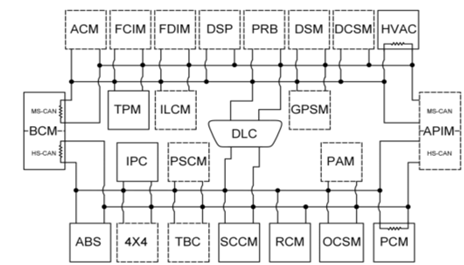
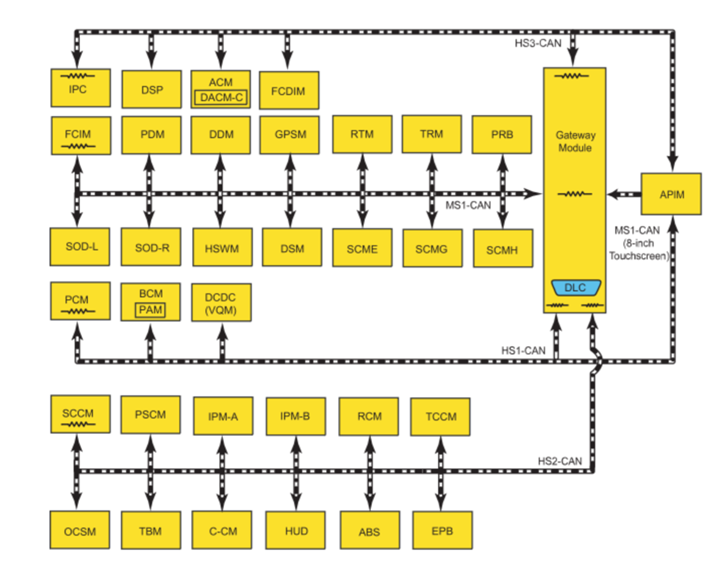
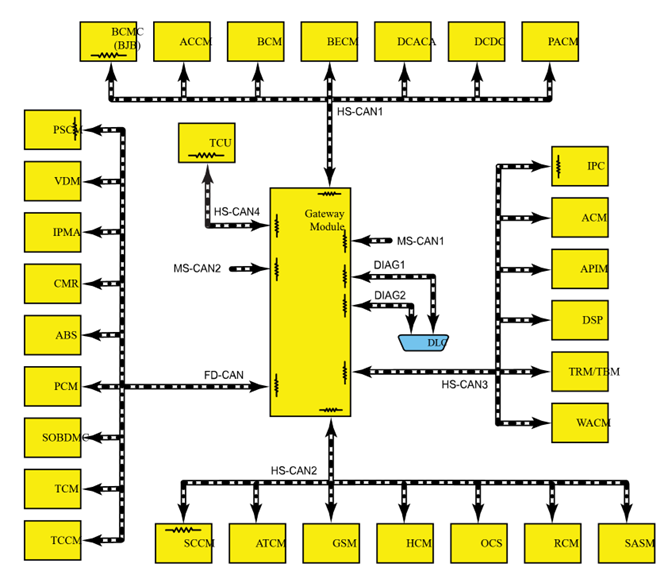
To fully understand these architecture trends and cybersecurity concerns, we take a deep dive through the Ford F-150’s E/E architecture. The three model years we will consider are 2011, 2015 and 2021. From the architecture diagrams shown below, the reader can get a sense of how the architecture has changed from an ad-hoc topology to a domain separated topology where a central gateway manages communications between individual domains. Overall trends are aligned with the earlier discussion and include an increase in the number of modules and buses in the recent years. To understand the cybersecurity implications of Ford F-150’s architecture, we now pick a specific approach that we call “attack path analysis.”
Figure E/E Architecture of Ford F-150 2011, 2015 and 2021 (left to right) as provided by Ford maintenance manuals.
Attack Path Analysis
Often, cyberattacks on vehicles have different origination and termination points. That is, the attack surface and attack target are not the same but connected by the E/E network. For example, an attack can originate from and compromise the telematics unit with the target to manipulate the modules on the drive train like brakes and steering. We call the path from the attack surface to the intended attack target an attack path. An attack path identifies cases where there is not enough separation between attack surfaces and critical modules. By labeling modules into categories depending on their position in the attack path, we can identify unsecure nodes that an attacker can compromise to reach the intended target.
The analysis starts by annotating car modules with short or long-range communication capabilities, which are existing threat vectors according to our threat model. Then, critical vehicle modules are identified, which are assumed to be the most important for the attacker, as DoS or direct control of such modules highly impacts the driving abilities of the vehicle and the safety of the driver. Modules that provide security related functions are treated specially. For example, Central Gateway modules often implement security functions and due to lack of additional proprietary information we assume that the gateway is hardened against possible cyberattacks and blocks attack paths. Finally, an automated analysis of the vehicle E/E network is run, and if a particular model has one or more attack vectors, a graph path search is performed between the module or modules with attack vectors and any module marked as “critical.” However, if there is a path that doesn’t cross the Central Gateway, it is marked as a valid attack path, and is displayed in the resulting visualizations. A valid path represents the possibility that the attacker can gain hold in the module with the attack vector and then gradually traverse between different modules until they can access the critical module or modules.
It’s important to note that a valid attack path only indicates a possibility of an attack and might not be feasible due to the lack of proprietary information. Furthermore, the difficulty of realizing the attack cannot be accurately analyzed without knowledge of the software of each of the modules and implemented cybersecurity mitigations. Our analysis can also miss possible attack paths due to incomplete information on attack surfaces, attack targets, and bus connections. In conclusion, the proposed analysis is neither complete nor sound, but it highlights the importance of cybersecurity in the automotive industry. We now discuss the individual three F150 models using our threat model.
Ford F-150 2011
The 2011 F-150 has a distributed network architecture and two attack vectors – A telematics module with long-range communication such as cellular, and Accessory Protocol Interface Module with short-range communication such as Bluetooth. The Power Steering Control Module is labeled as a security-critical module. As illustrated in the figure, the module can be reached by many possible paths (some shorter, some longer), so we mark this model as potentially vulnerable.
Ford F-150 2015
Our next example is the 2015 Ford F-150 in top trim. It has central gateway network architecture, so even though there is an attack vector (telematics module), it is on a different bus and protected by a central gateway so the attacker cannot reach the critical modules. We mark this model as not vulnerable according to our threat model.
Ford F-150 2021
The 2021 F-150 hybrid has a Sync Module that bypasses the central gateway and connects two different buses, shown in Figure 36. We can only speculate if this has been done for cost or performance reasons. As a result, the attacker can bypass the gateway and access the critical modules. Similarly, the image processing module is connected to two buses that should be kept separate. Again, we can only speculate if this was done for cost or performance reasons. As a result, this model is potentially vulnerable, despite having a central gateway.
Conclusion
There have been significant changes in the architecture of vehicle E/E networks over the years as they have evolved from distributed topologies to domain control topologies. Looking at the various vehicle models over the last ten years, we observe three distinct architectural topologies and we categorize them as distributed, control gateway and domain control architectures. An E/E architecture often does not neatly fall into one of these categories but will instead exhibit topological similarity to one or more. The below table captures our overall observations.
| Generation | Observed Architecture Classes | Key Features |
| 2010 | Distributed Architecture | Dominated by ad hoc connections between modules.Non-dedicated gateways: modules like body control modules may act as gateways. Few buses, consisting mostly of CAN and low bandwidth LIN buses. |
| 2015 | Central Gateway Architecture | Emergence of Central Gateways. Presence of some modules that appear to be domain controllers. |
| 2020 | Domain Control Architecture | Increase in the number of domain control modules with hierarchical sub-networks. |
| 2021 – Future | Centralized Architectures | Emergence of zonal consolidations (Tesla). |
This architectural shift has resulted in an increase in domain separation, network segmentation, and the use of newer bus technologies like CAN-FD and Ethernet buses. While there are positive cybersecurity implications of these changes, such as the ability to support stronger security features like encryption and intrusion detection and prevention, there are also potential concerns, such as an increase in the attack surface and impact area due to the increasing complexity and connectivity of modules and buses. Standardization and regulation of key modules and their security features, increased security for complex functions like ADAS modules and associated buses, and securing attack surfaces like OTA updates against remotely orchestrated attacks are some critical steps that the automakers can take to increase the cybersecurity of vehicles. Topologically secure architectures using techniques like network segmentation and other techniques are vital for providing a strong foundation for a safe and secure driving experience. It’s time for automakers to take action and prioritize cybersecurity to keep drivers safe on the road.
The post <strong>Vehicle E/E Architectures – The Last Ten Years and the Future</strong> appeared first on Galois, Inc..